Inside the Pyramid of Pain: Enhancing Cyber Threat Intelligence and Response
The Pyramid of Pain framework helps assess how difficult it becomes for attackers when defenders focus on particular indicators. The higher up the pyramid you go, the more disruptive your detection efforts are to the adversary’s operations or activities.
This content is adapted from TryHackMe’s Pyramid Of Pain.
1. Introduction
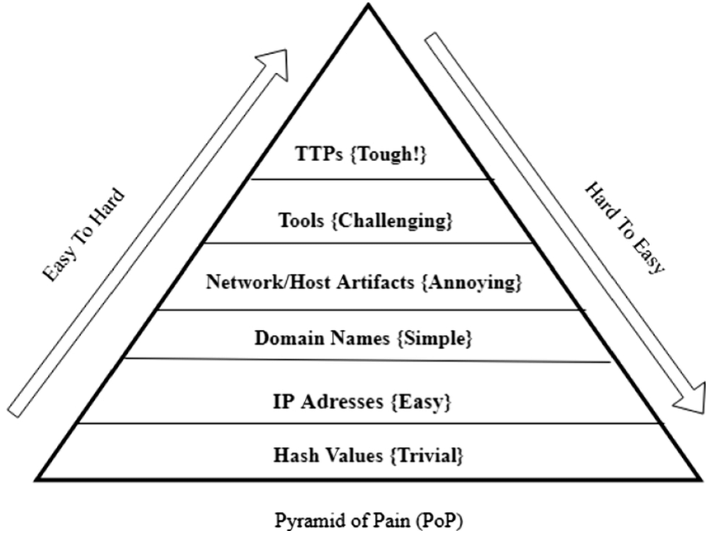
Key Concept: The Pyramid of Pain framework organises threat indicators according to the level of difficulty or disruption they pose for attackers to alter. It assists cybersecurity teams in identifying which indicators, when targeted, will most significantly disrupt or obstruct adversary activities.
Use it to:
- Focus defenses on indicators that are more impactful to attackers
- Raise the effort required for attackers to achieve their goals, potentially leading them to give up their attempts or alter tactics
Why It Matters for Security Teams
The Pyramid of Pain is essential for:
- Threat Hunters to comprehend the Pyramid of Pain in order to effectively spot and and disrupt adversaries.
- Incident Responders to understand the concept for better prioritisation and management of threats.
- SOC Analysts to apply the Pyramid of Pain in detecting and analyzing malicious activities.
Key Takeaway The objective isn’t just to detect threats—it’s to make attacks so expensive that adversaries decide to abandon their efforts.
Next Steps:
- Align your detection capabilities with the pyramid.
- Perform a gap analysis: Are you operating at a “Trivial” level or focusing on the “Tough” TTPs?
2. Hash Values in the Pyramid of Pain: A Practical Guide
A hash value is the output generated by a hashing algorithm when it processes an input, which can be a password or a file.
What Hashes Provide:
- Digital fingerprints for files (fixed-length alphanumeric strings)
- Quick identification of known malicious artifacts
- Common algorithms: MD5 (128-bit, deprecated for security), SHA-1 (160-bit, phased out by NIST), SHA-256 (256-bit, current gold standard)
Why Hashes Are “Trivial” in the Pyramid of Pain At the bottom of the Pyramid of Pain, hash values represent the easiest indicators for attackers to alter, requiring little effort to circumvent. While they are helpful for quick identification, they provide low adversary disruption because:
- A single bit change (e.g., appending text) completely alters the hash.
- Attackers can generate countless variations of malware, each with unique hashes.
How Security Teams Use Hashes
A. Initial Triage
- Tools: VirusTotal, MetaDefender Cloud
- Process: Input a hash (e.g.,
b8ef959a9176ae107dca870...) to:- Identify known malware (e.g.,
Tragin/Vary/APMCXw) - Review detection rates and community threat votes
- Identify known malware (e.g.,
B. Limitations
- Example: Modifying a file with
echo "AppendTheHash" >> file.exe
changes its MD5 from DJA808E3… to 90528A6F…, evading hash-based blocklists.
Hands-On Exercise
Task: Analyse the report associated with the hash “b8ef959a9176aef07fdca8705254a163b50b49a17217a4ff0107487f59d4a35d”
Goal: What is the filename of the sample?
Answer: Sales_Receipt 5606.xls
3. IP Addresses in the Pyramid of Pain: Balancing Utility and Limitations
Understanding the Importance of IP Addresses in Threat Detection
IP addresses play a crucial role in recognising endpoint devices on a network, including desktops, servers, and even Internet of Things devices such as security/CCTV cameras. In the context of cybersecurity and the Pyramid of Pain, IP addresses function as indicators of compromise (IOCs), helping to identify and prevent malicious activity.
In the Pyramid of Pain, IP addresses sit just above hash values and are categorised as “Easy” level indicators, representing a slightly more disruptive, yet still limited, indicator for defenders. They’re visualized in green, emphasising that while useful, these indicators offer limited long-term efficacy when used alone.
Defensive Use of IP Indicators
From a defensive standpoint (blue team), detecting and blocking potentially harmful IP addresses can assist in thwarting connections with known malicious networks. For instance:
- Blocking incoming or outgoing connections from suspicious IPs.
- Leveraging firewalls or intrusion prevention systems (IPS) to filter such traffic.
Nevertheless, experienced attackers can effortlessly circumvent this tactic by switching to new IP addresses or using methods like Fast Flux to rotate their infrastructure.
Example, Analysing Malicious IP connections from the TryHackMe Walkthrough (using app.any.run) In the analysis scenario:
- A malicious process (PID 1632) communicates with IPs like 50.87.136.52.
- It also uses a domain name like craftinglegacy.com, indicating C2 (Command & Control) behaviour. These malicious connections illustrate how attackers leverage IP addresses and domains for managing malware, stealing data, or issuing commands.
NOTE! Do not attempt to interact with the IP addresses nor domain names shown in the above example.
Fast Flux & Evasion Tactics
Attackers can complicate IP-based blocking through Fast Flux DNS, where a domain resolves to a constantly changing set of IP addresses:
- It serves as a proxy layer leveraging botnets.
- Helps malware maintain persistent communication with its command and control servers.
- Complicates detection and prevention efforts for defenders.
This tactic highlights the fragility of IP-based detection: IP addresses can change quickly, making them an unreliable sole indicator.
Pro Tip:
- Use IP addresses for initial triage, but invest in detecting how adversaries interact (e.g., unusual DNS requests).
Moving Up the Pyramid
- To increase adversary pain, target higher-level indicators like:
- Host/Network artifacts (e.g., C2 protocols).
- Tools/TTPs like detecting Fast Flux patterns through behavioural analytics.
Hands-On Exercise
Task: Analyse the report generated from any.run for this sample to answer the following questions:
- What is the first IP address the malicious process (PID 1632) attempts to communicate with?
- What is the first domain name the malicious process (PID 1632) attempts to communicate with?
Answer
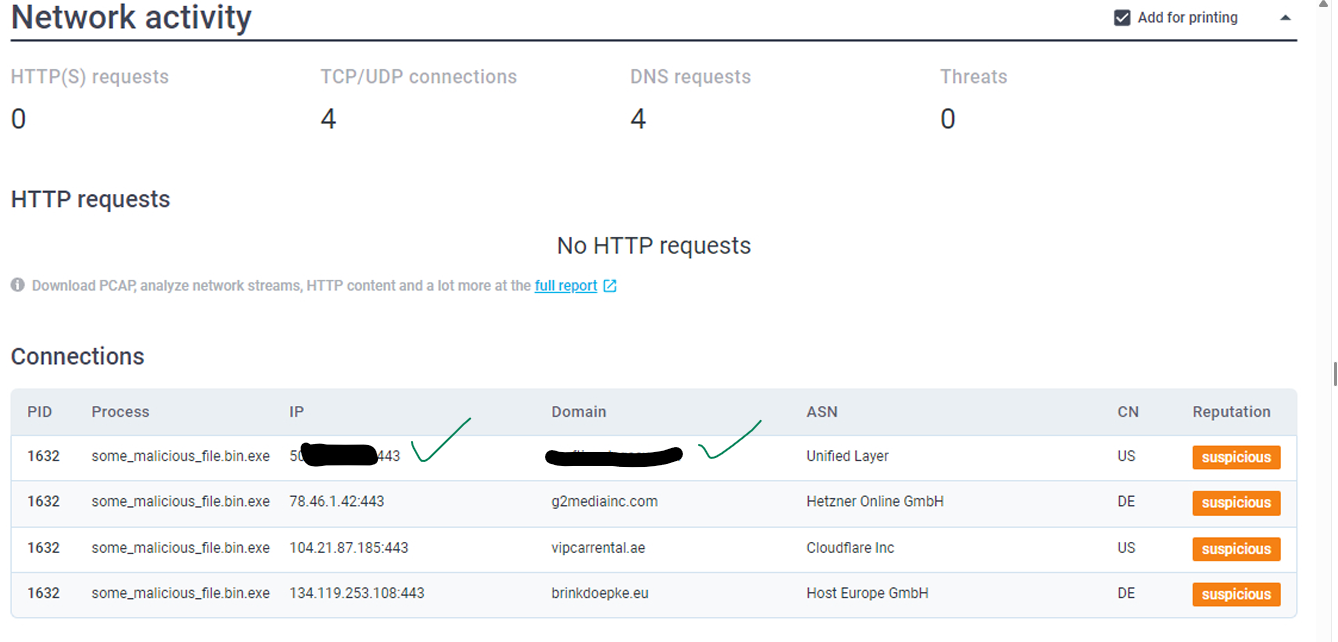
To answer the two questions above: Looking at page 5 of the any.run report and focusing on the “network activity” section of the report, we observe that
- the first IP address is listed in the first row and third column of the table associated with the first PID 1632 and the process name ‘some_malicous_file.bin.exe’.
- the first domain name is listed in the first row and fourth column of the table associated with the first PID 1632 and the process name ‘some_malicous_file.bin.exe’.
For additional illustrative information, refer to the table provided below:
4. Domain Names in the Pyramid of Pain: The “Simple” Tier
Transitioning from IP Addresses to Domain Names
As we move up the Pyramid of Pain, we encounter domain names, which are considered slightly more difficult for adversaries to substitute compared to IP addresses. This transition is illustrated in the colour change from green to teal in the pyramid graphic.
A domain name is essentially a readable string for humans that corresponds to an IP address — for instance:
- evilcorp.com (root domain + TLD)
- tryhackme.evilcorp.com (subdomain)
Domains provide a convenient and memorable means of accessing online resources and are extensively utilized by attackers for Command & Control (C2) operations.
Why Domain Names Are Important in Threat Detection
From the viewpoint of a defender:
- Domains serve as valuable indicators of compromise (IOCs).
- Domains tend to be more consistent than IP addresses, as the process of registering and configuring domains requires time and effort.
- Yet, attackers can still change domains frequently using dynamic DNS services or Fast Flux methods.
Unlike IPs, changing a domain often involves:
- Purchasing a new domain
- Configuring DNS records
- Propagating the infrastructure again
This process introduces challenges for the attacker’s operations, which is why domain names are more effective for detection and blocking compared to IP addresses.
Examples of Malicious Domains
TryHackMe lists examples of real-world malicious domains used in campaigns like Sodinokibi (REvil), illustrating how attackers create domains for delivering malware or communicating with compromised hosts. Some examples include: - dubero.com - tasteofwilliamsburg.com - revratka.com These domains are often crafted to appear harmless or to imitate genuine services.
Obfuscation Using Punycode A cunning strategy employed by attackers involves Punycode, where they leverage Unicode to visually mimic a recognized domain. For example:
- The malicious domain xn—addas-oa.de renders as adıdas.de in some browsers.
- This deceives users into clicking what seems to be a legitimate link.
This method is known as a Punycode attack, used in phishing and malware campaigns to trick users and evade visual scrutiny. Modern-day browsers like Internet Explorer, Google Chrome, Microsoft Edge, and Apple Safari have become quite adept at converting obfuscated characters into their complete Punycode domain names.
To detect malicious domains, proxy logs or web server logs may be used.
URL Shorteners for Redirection Cybercriminals often use URL shorteners to conceal their malicious domains:
- Services like bit.ly, tinyurl.com, or goo.gl obscure the final destination.
- A useful trick to reveal the real URL is to append a ”+” at the end (e.g., https://tinyurl.com/xyz+). This method is particularly beneficial for analysts to preview where a shortened link ultimately leads before clicking on it.
Using Any.run for Domain Analysis In sandbox environments like Any.run, you can: - Monitor DNS queries to determine if malware is attempting to resolve domains. - Monitor HTTP requests to track interactions with malicious servers. - View Connections (TCP/UDP) that may suggest C2 traffic activity or data exfiltration.
For example, a suspicious domain like craftingalegacy.com may appear as the first IOC in a malware execution trace, indicating its role in the infection chain.
Hands-On Exercise
-
Go to this report on app.any.run and provide the first suspicious domain request you are seeing, you will be using this report to answer the remaining questions of this task.
- Answer: Looking at the first row of the ‘Connections’ tab of the report will reveal the first suspicious domain request.
-
What term refers to an address used to access websites?
- Answer: Domain Name is the address used to access websites (for example, on the internet).
-
What type of attack uses Unicode characters in the domain name to imitate a known domain?
- Answer: A Punycode attack (a type of homograph attack) occurs when an attacker registers a similar domain using Unicode characters that mimic Latin letters, and subsequently encodes it in Punycode to register it as a legitimate domain.
-
Provide the redirected website for the shortened URL using a preview: https://tinyurl.com/bw7t8p4u
- Answer: To preview the destination of a shortened URL before clicking on it, we can append a plus sign (+) to the end of the TinyURL link, as shown:
This will direct us to a preview page that displays the final destination URL, allowing us to confirm its safety and legitimacy. Therefore, the shortened URL https://tinyurl.com/bw7t8p4u redirects to https://tryhackme.com/
5. Leveraging Host Artifacts to Disrupt Attackers: The ‘Annoying’ Tier of Pyramid of Pain
Introduction
This phase signifies a significant jump in the challenge for the attacker. Host artifacts are positioned in the yellow zone of the Pyramid of Pain and are considered “annoying” for adversaries. When defenders successfully identify these indicators, attackers are forced to change their tools, behaviours, or possibly even their entire approaches, which requires them to expend time, effort, and resources.